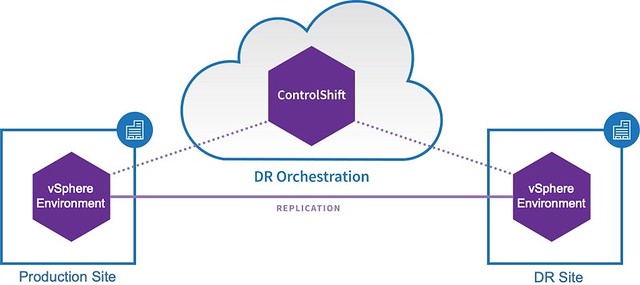
During my time at Datrium, I’ve been hearing more and more CIO’s and Head’s of IT say the following line whilst our Sales teams are pitching the Datrium Automatrix Platform.
This sounds too good to be true!
The reason why Automatrix is classed as “too good to be true” is because of what we as an IT industry have become accustomed to. We accept and expect IT systems to be complex to manage, maintain and require training to operate. It’s a given that you will need to use multiple vendor solutions in order to meet your business requirements.
So when a solution is presented to us that contradicts our many years of IT experience, we immediately pass it off as “too good to be true”, even if in fact, it is true!
Take for example VMware. We all know and love VMware and their products. However, it didn’t always use to be this way. Back in the early early days of VMware, adoption of VMware Server, as it was called then, was almost limited to use as a Disaster Recovery option as it wasn’t deemed something that could be used in production. Not because it wasn’t production-ready, but because it was “too good to be true” and no one believed that it could do what VMware said it could do.
It’s frustrating when you know first-hand how good something is, but other people don’t seem to want to listen to what you are telling them, especially when you know that they will benefit from it.
I recently read a fantastic article from James Clear; Why Don’t Facts Change Our Minds and I think much of what James talks about in his article relates to what I am seeing within the industry.
Truth and accuracy are not the only things that matter to the human mind. Humans also seem to have a deep desire to belong. Humans are herd animals. We want to fit in, to bond with others, and to earn the respect and approval of our peers. We don’t always believe things because they are correct. Sometimes we believe things because they make us look good to the people we care about.
If a brain anticipates that it will be rewarded for adopting a particular belief, it’s perfectly happy to do so, and doesn’t much care where the reward comes from — whether it’s pragmatic (better outcomes resulting from better decisions), social (better treatment from one’s peers), or some mix of the two.”
I think because of what James talks about, IT folk find it difficult to go against the status quo, even if a new product can be highly beneficial to a business. And I get it. We all want to fit in and be accepted by others, even if it holds many of us back.

Summary
During my time in the industry, I’ve actually found that going against the crowd, whilst as difficult as it is, can often bring us the most success. Not everything works out, but when it does, it’s massive and usually a game-changer for you and your company.
So if you see/hear something that you think “This is too good to be true!”, don’t just push it aside. It could actually be true and you are going miss out on all of the value you will get from it. Take the pragmatic approach. Dig deeper. This could be a diamond in the rough.
Datrium is not “too good to be true!”. It is actually true! We can prove it. If you’ll let us of course.
Here are some fun (non-IT) examples of where I wished I had taken the pragmatic approach rather than listening to my social circles.
- Cold Brew Coffee – Growing up in England, Coffee was always hot. If it was cold, you’d pour it away. Now I can’t get enough of the stuff!
- Tempur-Pedic Mattress – Quite possibly one of the best purchases I ever made. They cost an arm and a leg, but OMG it’s soo comfortable. Even though TV commercials told me how good they were, I thought they were “Too good to be true”. Then I had a hotel room with one in and I’ve never looked back.
- Yeti Tumbler – How good can a cup really be? Do I really need my drink to be kept cold/hot? I thought not. I got one as a gift for my birthday and I’ve pretty much used it every day since. I’ve even brought one for other people I know who’d love it, but like me, thought it was “Too good to be true”.